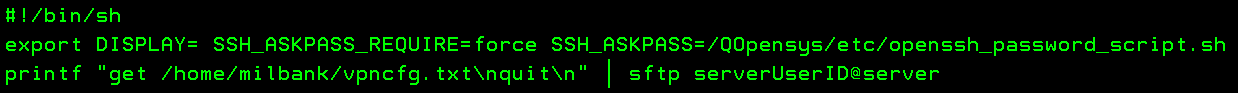
EDTF '/QOpenSys/etc/openssh_password_script.sh'
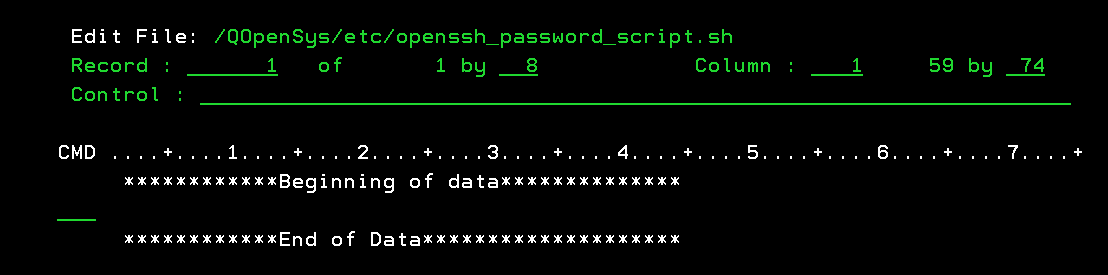
Press F15 to enter the Edit File Options Screen.
The password shell script must have UNIX-style line ends (LF) at the ends of lines rather than (CR/LF) like on Microsoft Windows-based machines.
Entering option 5 on the Selection line and then specify *LF for the Stream file EOL option to append a line-feed at the end of each line in the file.

Press the enter key for the EOL change to take effect.
Press F3 to exit the Edit File Options screen.
Store the password for the user account that the SFTP server administrator provided in the password script file.

Note: The prefix area in the CMD column is used for entering edit commands. For example, typing
In can insert
n blank lines after the record. Conversely, you can use
Dn to delete the current line and the next
n-1 lines or
D to delete one line.
Here's a brief description of each record in the password script file:
#!/bin/sh -> Specifies the shell that interprets commands in the script file.printf -> Prints the password for the user account that the SFTP server administrator provided to transfer files.Press F3 to Save and Exit the password shell script.